Logger - HTB Forensics
Challenge Description
A client reported that a PC might have been infected, as it’s running slow. We’ve collected all the evidence from the suspect workstation, and found a suspicious trace of USB traffic. Can you identify the compromised data?
Analysis
We are given one capture file (keystrokes.pcapng) to solve this challenge. Let’s open it with Wireshark.
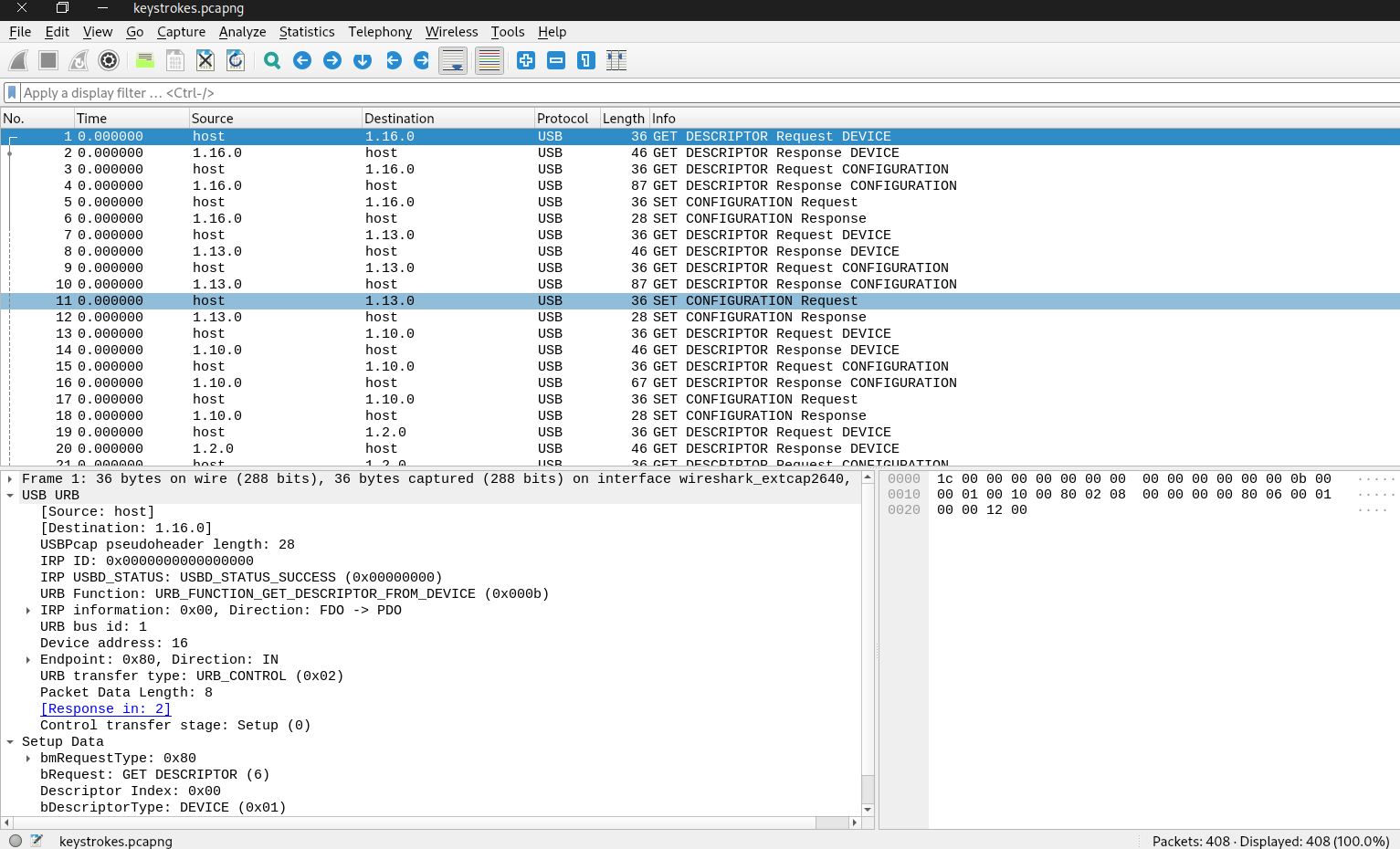
This is my first time seeing this kind of a capture file. Because the protocol of the capture is 100% USB. But from the challenge name, we can get a hint that we are hunting for a keystroke logging. Anyways, Looking at the statistics of the capture file, we cannot find any information there. There are no conversations or endpoints associated with the capture file. Looking at the packet info in Wireshark, we can see device configuration requests and responses, and descriptor requests and responses for configurations as well as for the devices.
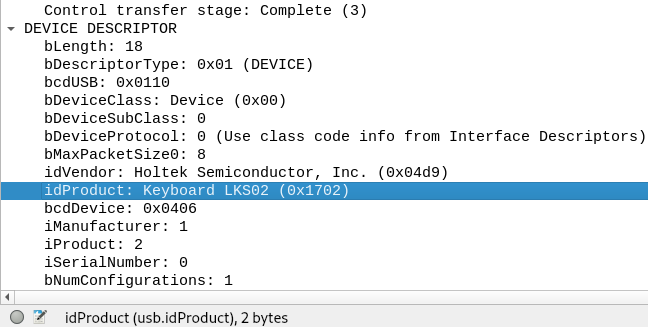
Let’s keep our eye on packet details pane of Wireshark and go through several packets. The packets with info ‘Descriptor response device’ contains an interesting information under device descriptor. This is for sure device’s response to a specific key stroke. We see a keyboard Lks02 and an optical gaming mouse as input devices here in our capture. Let’s first focus on the responses for the keyboard.
But how can we extract the data communicated? If you do some research you’ll find that USBHID is a windows protocol that allows USB devices to talk with Windows OS. So in our case when a key is pressed on the keyboard, the signal is sent to the computer using USBHID. So, we need to focus on the packets that sent from the device to our host. The data is in the USBHID field.
let’s filter out the traffic originated from usb keyboard and then extract the HID data. 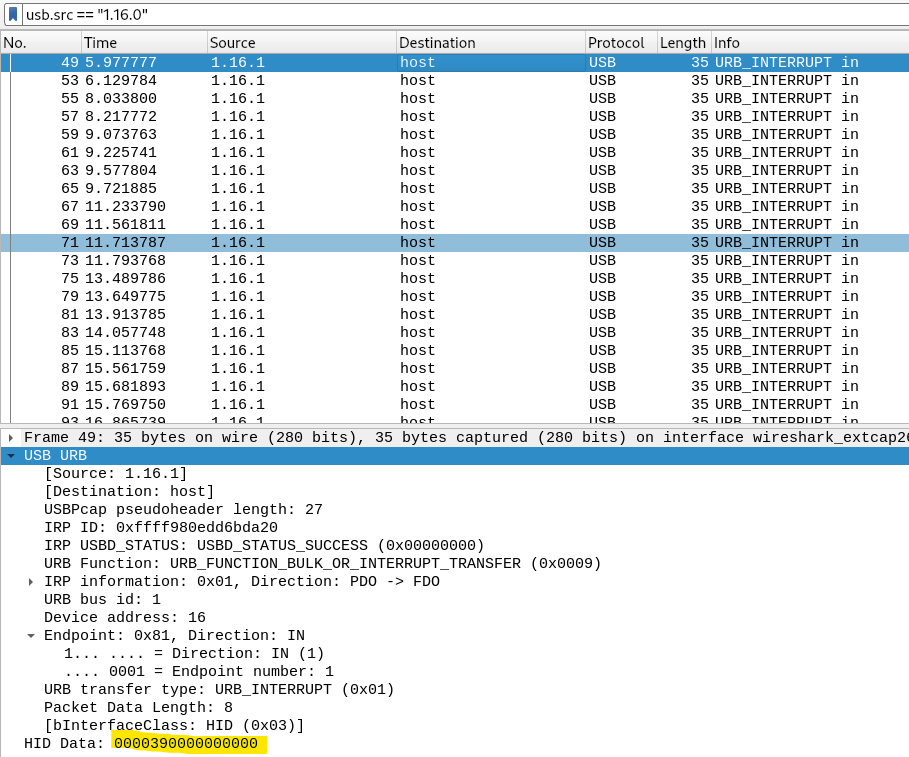
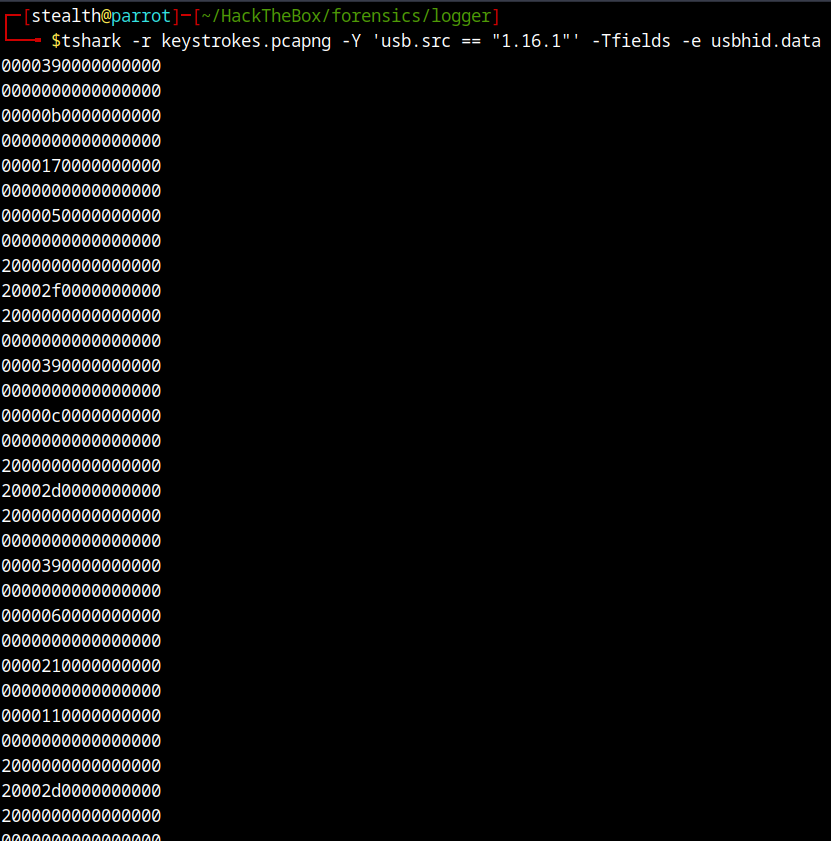
There are total of 76 packets here and exactly half of them contains HID data which is key strokes. it would be a nightmare to extract the data, manually one by one in wireshark. So, let’s use tshark and extract our data.
Solution
We can directly use wireshark’s display filter we applied, in tshark using flag -Y. Then we need to mention what fields are we extracting data from using -Tfields -e.
1
tshark -r keystrokes.pcapng -Y 'usb.src == "1.16.1"' -Tfields -e usbhid.data
But still it’s not human readable. I found a python script which allows us to extract hid data in ASCII. But we need to arrange our extracted hid data first in the format of xx:xx:xx:xx:xx:xx.
We can do this with a simple command.
1
cat keystrokes.txt | sed 's/../:&/g2' >> hid.txt
Here is the link to the python script. https://github.com/TeamRocketIst/ctf-usb-keyboard-parser
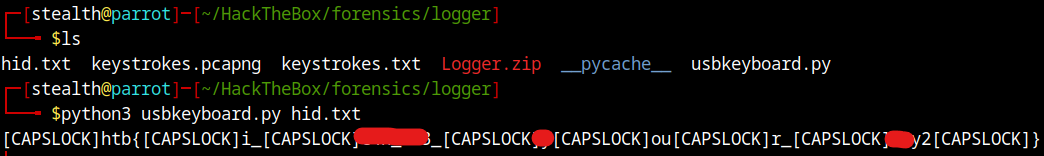
We simply need to run the script and we are given our flag. Anyways, we have to change in between where capslock is pressed in order to correctly get the flag.
Lessons learned
The Logger - HTB Forensics challenge provided valuable insights into USB HID protocols and packet analysis techniques. By dissecting USB traffic using Wireshark and tshark, we learned to filter and extract HID data efficiently.